LS-Auth integration with Login.gov as IDP (SAML)
Below are instructions to set up Login.gov as an IDP for LSAuth using SAML.
NOTE: Integration will need to be done against Logn.gov sanbox env.After testing is completed. the app will be promoted to prod by Login.gov team upon request.Please follow the https://developers.login.gov/ for more info
Create an Identity Provider Configuration in LSAuth
-
Note down the IDP details from the Login.gov meta data available below (Note: change the year at the end of the URL accordingly). Note down EntityID, SingleSignOnService (Post) Location,SingleSignOnService Location (Optional), Copy the IDP X509Certificate value to a .cer file
-
Generate a SP X509 certificate with public private keys using openssl or keytool to be used as signing cert for AuthNRequest
IDP metadata for Login.gov sandbox :
https://idp.int.identitysandbox.gov/api/saml/metadata2020
IDP metadta for Login.gov production:
https://secure.login.gov/api/saml/metadata2020
-
Log into the LS Auth console for and select the tenant that you will use.
-
Select “Providers” in the left nav menu and click the “Add New” button.
-
Select Provider Type “SAML2”
-
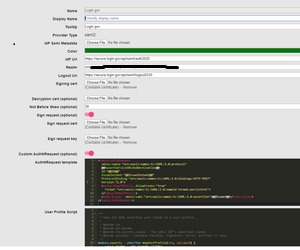
Update the following details
IDP URL (SSO URL copied from above):
https://secure.login.gov/api/saml/auth2020
Logout URL (IDP Logout URL):
https://secure.login.gov/api/saml/logout2020
Realm Set a unique string (eg format:
urn:gov:gsa:SAML:2.0.profiles:sp:sso:NCATS:auth.ncats)
Signing Cert: IDP certificate you saved above
-
Enable Sign Request ,upload the Public and private SP certificates generated above.
-
Enable Custom AuthNRequest and enter the following format in the script box
<samlp:AuthnRequestxmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"@\@AssertServiceURLAndDestination@\@ID="@\@ID@@"IssueInstant="@\@IssueInstant@@"ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"Version="2.0"><samlp:NameIDPolicy AllowCreate="true"Format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent"></samlp:NameIDPolicy><saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">@\@Issuer@@</saml:Issuer></samlp:AuthnRequest>
- Use “User Profile Script” editor to set claim mappings. Copy the
below script into the “User profile Script” block
Note: Additional claims mapping options are also available in the application configuration.
module.exports = function mapUserProfile(ctx, callback) {
const claims = ctx.secrets.claims;
const profile = {
email: claims.email,
upn: claims.uuid
};
callback(null, profile);
}
Creating application on [Login.gov]{.ul}
-
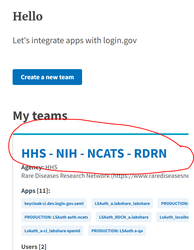
Request for admin account to Login.giv sandbox / partner dashboard following instructions in https://developers.login.gov/ (Get added to our test sandbox environment) and set up MFA for the account once its added. NOTE: For NCATS RDCRN project we are using team “HHS - NIH - NCATS - RDCRN”
-
Sign in using your admin account to https://dashboard.int.identitysandbox.gov/
-
You should see a team you are by default assigned to
- Access “APPS” on the top right corner and click on 'Create a new test app'
5. Enter the App details Eg: shown below (Select a different name), Select Authentication protocol as SAML. Issue has to be same as the “Realm” configured above in LSAuth .
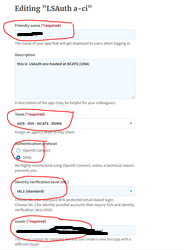
6. Enter the SP public key generated above (Used for signing the AuthNrequest on LSAuth).
Enter the ACS URL and Logout URL accordingly from LS-Auth: Quick Links
Disable Assertion Encryption and make sure “email “ is selected in the attributes.
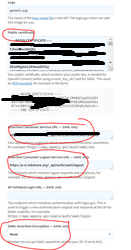
7. Save the application.